Where does Russian Malicious Cyber Activity come from (according to US Homeland Security declassified files)
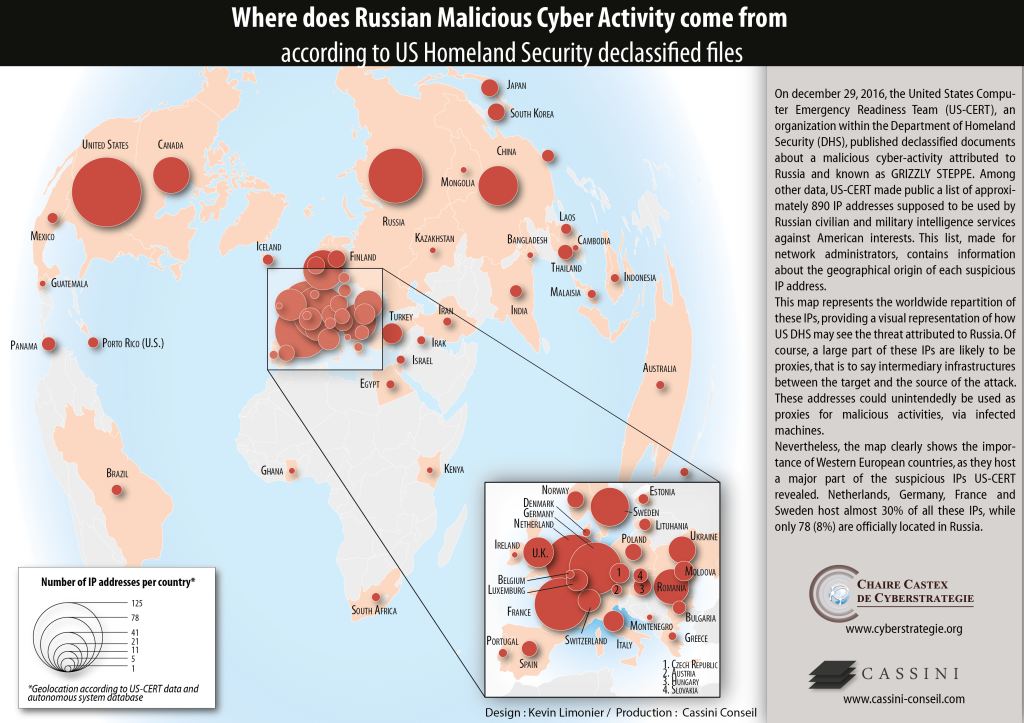
On december 29, 2016, the United States Computer Emergency Readiness Team (US-CERT), an organization within the Department of Homeland Security (DHS), published declassified documents about a malicious cyber-activity attributed to Russia and known as GRIZZLY STEPPE. Among other data, US-CERT made public a list of approximately 890 IP addresses supposed to be used by Russian civilian and military intelligence services against American interests. This list, made for network administrators, contains information about the geographical origin of each suspicious IP address.
This map represents the worldwide repartition of these IPs, providing a visual representation of how US DHS may see the threat attributed to Russia. Of course, a large part of these IPs are likely to be proxies, that is to say intermediary infrastructures between the target and the source of the attack. These addresses could unintendedly be used as proxies for malicious activities, via infected machines.
Nevertheless, the map clearly shows the importance of Western European countries, as they host a major part of the suspicious IPs US-CERT revealed. Netherlands, Germany, France and Sweden host almost 30% of all these IPs, while only 78 (8%) are officially located in Russia.